Steps to AIOps maturity: Establish actionable incidents
Lack of communication between IT operations and ITSM teams results in data silos. And data silos make it challenging, if not impossible, to solve problems efficiently. One-third of ITOps professionals say that gathering business context is the biggest challenge to effective incident response and management, according to EMA Research.
In the path to AIOps maturity, phase 2 focuses on establishing actionable incidents. In the crucial first phase, we set a foundation by integrating and standardizing disparate data sources for quick readability. Identifying what’s actionable requires a clear understanding of incident scope and impact to give operators a perspective of each incident. This means correlating alerts across multiple monitoring tools into one actionable incident. With in-depth, cross-system insights at their fingertips, operators and responders can reduce analysis and response times, ultimately preparing for the use of AI in the latter stages.
“When you have very low-quality alerts that are just making high volumes of noise, you cannot act on them because you can’t make sense of what’s actually happening within the environment or how critical the alert is.”
Priscilliano Flores
Staff Software Systems Engineer, Sony Interactive Entertainment
Understanding incident scope and impact
With a comprehensive understanding of scope and impact, operators gain a holistic view of the situation. This broader perspective is crucial for making informed decisions quickly and accurately. Instead of isolated alerts creating noise and confusion, correlation lets teams focus on the most significant issues affecting service availability and performance.
Admittedly, it’s easier said than done. The sheer volume of alerts often overwhelms operators, leading to missed or delayed response to critical incidents. Tool sprawl and data silos fragment data, making it difficult to see the full context. With siloed data, teams need to manually correlate alerts across each system, a time-consuming and error-prone process that increases MTTR and reduces efficiency.
When you implement multidimensional correlation across all data sources, operators gain improved visibility of what’s happening and why. They can quickly see the incident context, understand the root cause, and reduce their response time to deliver results more efficiently.
Establishing actionable incidents
Creating actionability to deliver greater incident context, faster analysis, and less manual effort requires collaboration among all teams involved in incident response. Although every organization is unique, these teams typically include IT operations, incident management, problem management, and enterprise architecture.
Phase 2 involves three key actions enabled by the BigPanda platform:
- Incident tagging: Creating tags is fundamental to improving incident correlation and automation. Tags such as “priority” help categorize incidents for better troubleshooting. Additionally, setting up environments that group incidents — such as all U.S.–based or AWS-related incidents — enables more focused and efficient triage.
- Event correlation: Ensure that operators focus on the most relevant, impactful incidents. Incident tags support building patterns that correlate alerts across all data sources, tools, and platforms. From there, you can validate and measure patterns for efficacy using the correlation patterns dashboard in BigPanda Unified Analytics.
- Automation: A significant element of incident management, automating ticket creation and data population within the ITSM platform streamlines the initial incident response. Integrating downstream actions — such as chat, collaboration, or remediation tasks within external tools — also ensures a seamless and coordinated incident response.
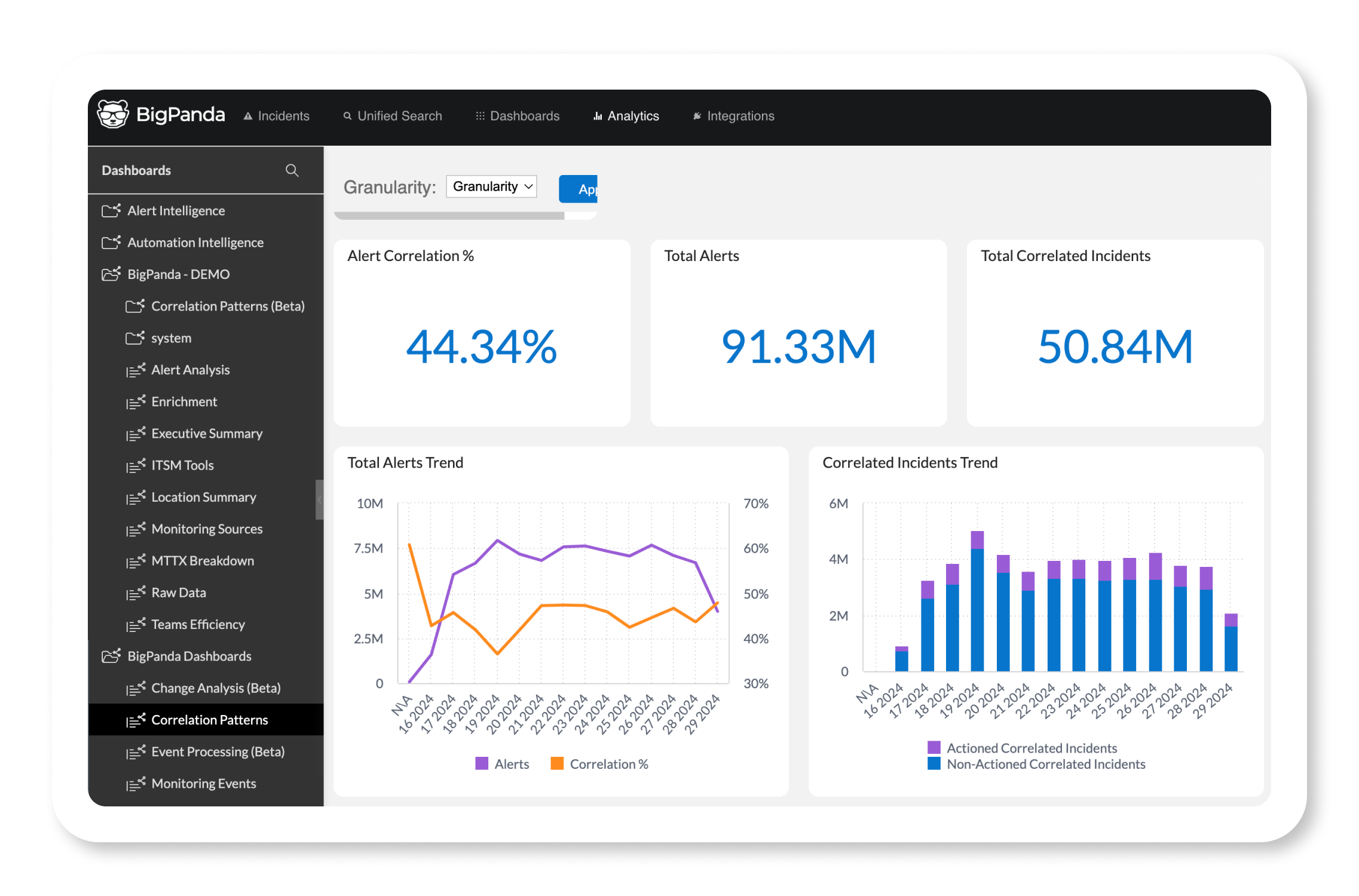
Many organizations find actionability on alerts and incidents elusive, but it doesn’t have to be when you reach this level of AIOps maturity. Enhancing incident response and results by correlating alerts across multiple monitoring tools into actionable incidents is a transformative approach with multiple benefits.
Defining success
If you don’t define metrics, you won’t know what’s working or what isn’t. Improved incident correlation is a primary success measurement in Phase 2. Higher correlation rates indicate that you’re accurately grouping more alerts into actionable incidents, reducing alert noise, and improving focus.
Providing teams with in-depth cross-system insights can reduce MTTR, improve efficiency, support SLA compliance, and ensure consistent service availability. This approach sets the stage to take advantage of generative AI, positioning your organization for continued success in the evolving landscape of IT operations.
For an overview of the four phases, download the “Practical guide to AIOps maturity” e-book or explore the phases in our post series:
- Phase 1: Reducing alert noise
- Phase 3: Reducing MTTR with AI (coming soon)