How to improve IT alert management: Best practices
As an IT leader, you’re under significant pressure to control the constant alerts. Somehow, you must manage non-stop IT alerts while also ensuring ultra-high service availability. The task is far from easy, and even the most sophisticated teams struggle to keep up and turn alerts into action with tech stacks that are constantly growing in size and complexity.
IT alert management is the first line of defense. By managing the alert process, you can better ensure that IT alerts don’t escalate into costly service disruptions. That’s why improved enterprise IT monitoring begins with better IT alert management.
So, if you want to enhance your alert management, understand the alerting process, discover best practices, and learn how AIOps can streamline your alerting, you’ve come to the right place.
Read on to learn:
- What is alert management in IT?
- How does the alert management process work?
- Best practices for alert management teams
- Best practices for alert management tools
- How Sony overcame common challenges with IT alert management with AIOps
What is alert management in IT?
IT alert management is a systematic process of monitoring, analyzing, and responding to alerts from IT systems. These alerts are triggered by changes or failures that signal disruptions or degradations in services within an organization’s IT system. Managing alerts ensures faster resolution, reduced alert noise, fewer escalations, and proactive identification and resolution of critical alerts.
What are the steps of the alert management process?
Alert management in IT seeks to enhance the monitoring and response capabilities of an organization’s IT infrastructure and proactively identify potential issues. Here’s a simplified breakdown of how it works:
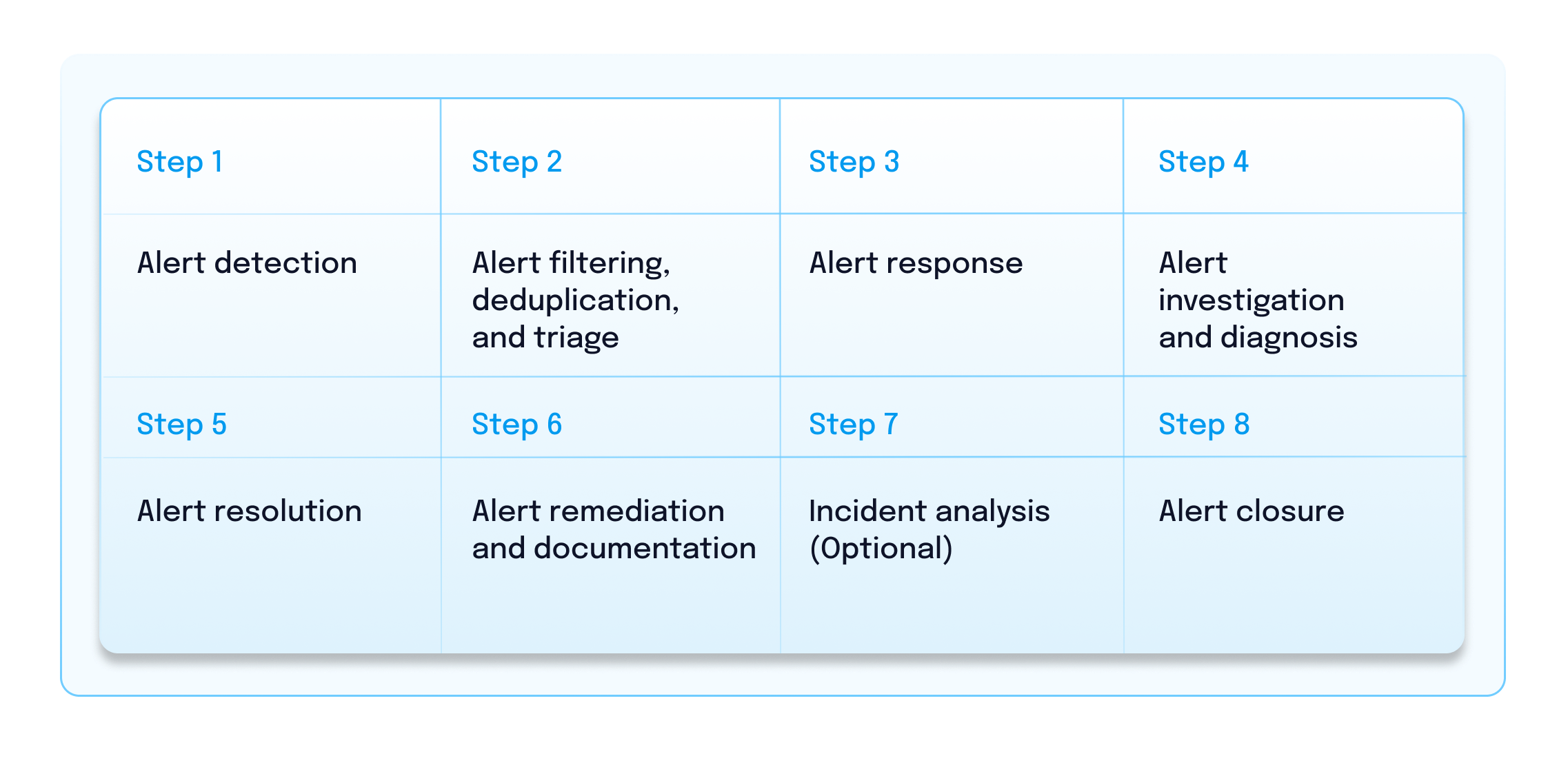
Step 1: Alert detection
In the alert discovery stage, monitoring tools observe the IT environment in real time for predefined conditions, such as high-risk actions, system changes, or failures. When these tools detect an anomaly or issue that meets the predefined criteria, they generate alerts and are sent to either a centralized Network Operation Center, SRE, or specific DevOps teams to respond to
Step 2: Alert filtering, deduplication, and triage
Traditionally, alert triage is a manual process done by IT personnel assessing the alerts to determine their severity and impact on the system. Alerts are then categorized based on predefined criteria to prioritize responses.
This process is typically done by an alert management feature within the ticketing platform, a monitoring solution, or an AIOps solution. AIOps solutions filter, deduplicate, and normalize alerts from different systems and use AI/ML to identify correlation patterns across thousands or millions of alerts across all monitoring tools.
Alert enrichment is an essential part of this stage. By enriching alerts with vital metadata, ITOps teams gain insight into dependencies, while correlation and alert grouping ensure teams can quickly review all alerts related to an incident to accelerate triage activities.
Step 3: Alert response
Now that your alerts have been condensed and enriched with vital context, you need to get them to the right stakeholders, such as IT admins and support teams for resolution.
Most teams use ticketing or a monitoring solution for their alert response workflows. You’ll want to ensure this platform, whether ServiceNow, PagerDuty, or other solutions uses automation or is paired with an AIOps tool to update tickets and share incidents with the right teams automatically.
Step 4: Alert investigation and diagnosis
Critical alerts will trigger the creation of an incident or an adverse IT event. Incidents document details about the problem, such as its nature, location, and any other pertinent information. Responders will investigate these alerts and incidents for resolution. AI/ML can speed up this process by automating root cause investigation.
Step 5: Alert resolution
Once the cause is identified, the team works on resolving the issue. This could involve applying fixes, restarting services, replacing hardware, or updating software. For previously known issues with established solutions, AIOps and IT alert management systems can suggest predefined resolution procedures to quickly address common or routine problems with minimal human intervention.
Step 6: Alert remediation and documentation
The actions and resolutions applied are documented in the IT alert management system along with any other relevant information throughout this stage. This documentation is helpful for reference in future alerts and incidents and for reporting to stakeholders.
Step 7: Incident analysis (optional)
An analysis is only done for critical rather than everyday incidents. IT teams can conduct their post-incident analysis manually or automatically for these major incidents or outages. An analysis is conducted to understand the root cause, identify trends, and implement preventive measures for future occurrences.
Step 8: Alert closure
Once the issue is resolved and all analyses and documentation are complete, the alert can be officially closed. Closure indicates that the incident is fully addressed, and no further action is required. This phase is crucial for learning from the incident and improving future responses.
Best practices for alert management teams
Implementing the right processes for IT alert management teams is essential, as it cultivates a streamlined and coordinated response. Improved practices minimize downtime and ensure critical issues are addressed promptly and effectively.
- Ensure cross-team alignment: Alignment success comes from teamwork across different departments, fostering a culture of ownership and commitment to enhancing alert and incident quality. Similarly, you should ensure your IT department works together on alert processes.
- Continuous improvement and compliance: Create a feedback loop to improve alert quality standards continually. Use analytics to measure incident management performance, adjusting their strategies as needed. Additionally, maintain compliance with alert standards and ensure transparency in the alert management process.
- Regularly monitor alert hygiene: Maintain your organization’s alerting environment to ensure timely alert categorization, escalation, and resolution. Good maintenance guarantees accurate measurement of monitoring KPIs and prevents skewed metrics caused by intermittent bulk actions.
Best practices for alert management tools
Grasping the intricacies of IT alert management tool requirements is crucial, as it ensures that organizations choose solutions adept at filtering the signal from the noise to enhance efficiency and reduce response times in critical situations.
- Centralized visibility: Use a single dashboard for unified visibility across different monitoring tools. This will help you organize and prioritize alerts, making it simpler to respond to critical incidents.
- Alert standardization: Develop and enforce alert standards to ensure they have all necessary context for quick and efficient resolution. Standardization ensures alerts have enough contextual data for support teams to act promptly.
- Incident intelligence through AIOps: Leverage Artificial Intelligence for IT operations to transform alert data into contextualized, actionable, and high-quality intelligent alerts for easier management. With AIOps, you can use incident intelligence tools to enhance overall alert management efficacy.
Case Study: How Sony overcame IT alert management challenges
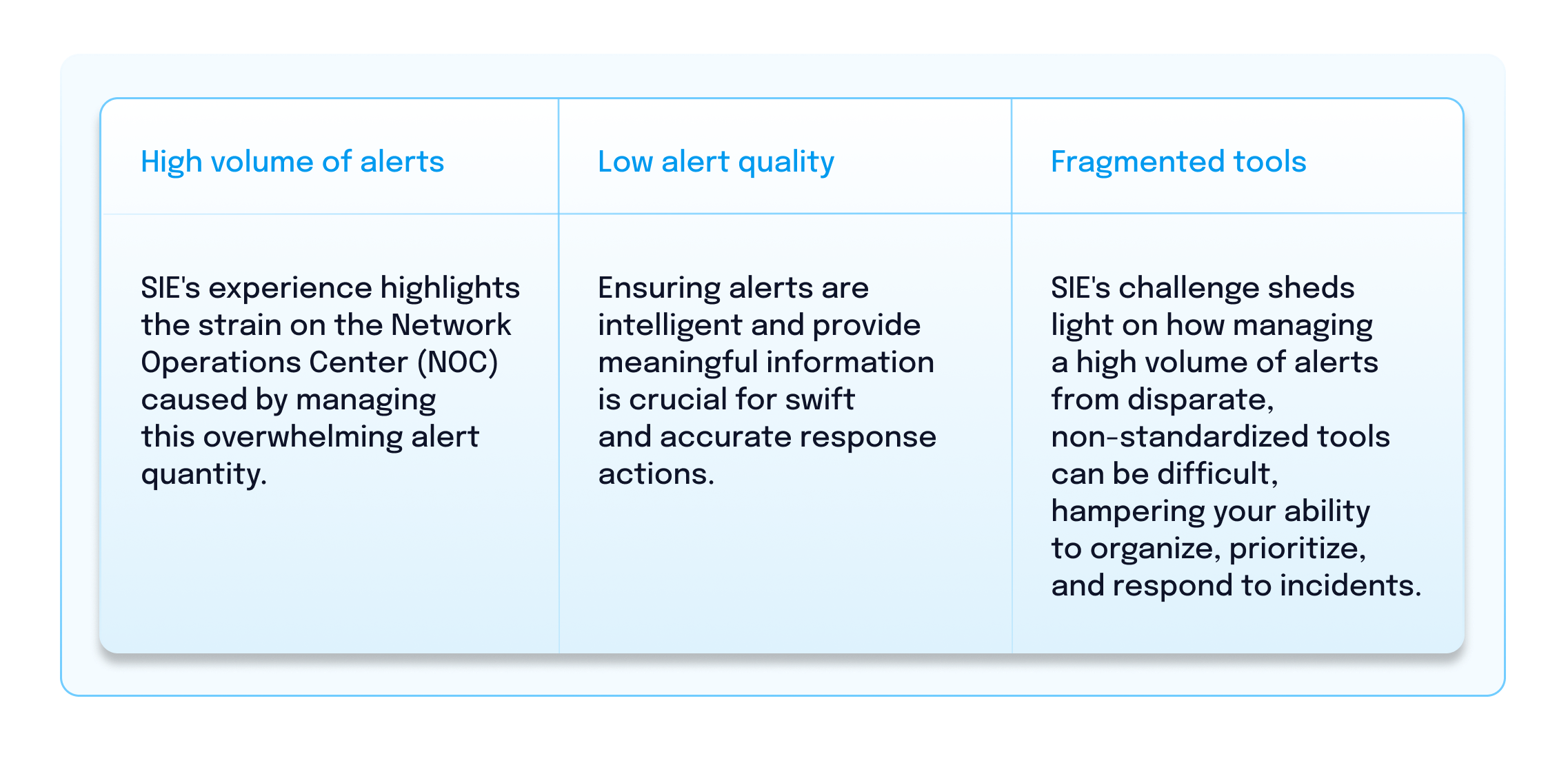
BigPanda customer Sony Interactive Entertainment’s (SIE) Network Operations Center faced significant challenges when inundated by a high volume of low-quality alerts from fragmented, siloed tools.
This struggle not only put service quality at risk for users and partners but also highlighted issues like alert fatigue, delays in responding due to insufficient information in alerts, and the increased complexity due to using disparate tools in problem resolution.
SIE’s experience underscores the following three key challenges organizations should anticipate in alert management:
BigPanda helps SIE to better prioritize and manage alerts from multiple monitoring tools to improve efficiency in addressing and resolving incidents. This improvement is gradually changing the internal culture at SIE, encouraging the broader adoption of AIOps across additional teams.
“[Operators] started seeing the potential of using BigPanda and not only embraced it but also evangelized it across other teams.”
— Priscilliano Flores, Staff Software Systems Engineer at Sony Interactive Entertainment
Improve your alert management processes with Alert Intelligence from BigPanda
Whether you’re ready to combat alert fatigue from a multitude of alerts or concerned about how poor alert management can lead to costly downtime, you know that better alert intelligence is pivotal. It impacts your business’s bottom line and alleviates your IT teams from high workloads and higher stress levels.
- Enhance your alert management processes: Use BigPanda Alert Intelligence to streamline your alerts and reduce IT noise. Filter out false positives and recurring events, ensuring that only high-quality alerts reach your ITOps teams.
- Alerts made actionable: Transform low-quality alerts into actionable incidents, enabling more efficient triage and troubleshooting.
- Gain visibility and ease collaboration: Aggregate high-quality alerts into a unified view, making it easier for teams to navigate different tool consoles when addressing incidents.
BigPanda takes a comprehensive approach to alert management, allowing your response team to focus on relevant issues, leading to more effective incident resolution. Get a demo to learn more about how BigPanda can transform your alert management.